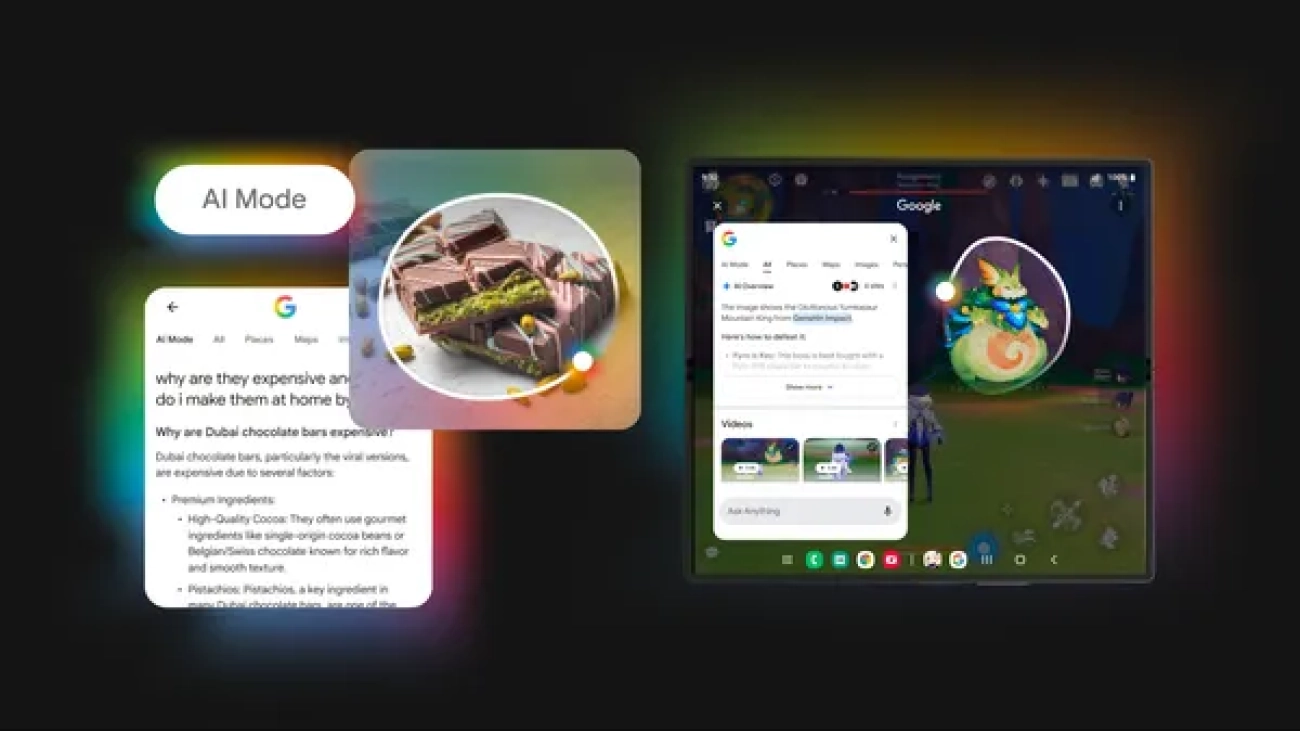
We’re bringing new AI capabilities to Circle to Search, so you can dive deeper and ask follow-ups in AI Mode, and get gaming tips.Read More
We’re bringing new AI capabilities to Circle to Search, so you can dive deeper and ask follow-ups in AI Mode, and get gaming tips.Read More
How Lush and Google Cloud AI are reinventing retail checkout
 Cosmetics company Lush is embracing Google Cloud AI to improve how they work.Read More
Cosmetics company Lush is embracing Google Cloud AI to improve how they work.Read More
New AI tools for mental health research and treatment
 This field guide and investment support AI’s potential in evidence-based mental health interventions and research.Read More
This field guide and investment support AI’s potential in evidence-based mental health interventions and research.Read More
The latest AI news we announced in June
 Here are Google’s latest AI updates from June 2025Read More
Here are Google’s latest AI updates from June 2025Read More
We used Veo to animate archive photography from the Harley-Davidson Museum
 In Moving Archives, we’re bringing the iconic Harley-Davidson Museum archives to life with the help of Veo and Gemini.Read More
In Moving Archives, we’re bringing the iconic Harley-Davidson Museum archives to life with the help of Veo and Gemini.Read More
Expanded access to Google Vids and no-cost AI tools in Classroom
 Learn more about expanded access to Google Vids for all education users, and Gemini in Classroom, a new suite of no-cost AI tools available for educators.Read More
Learn more about expanded access to Google Vids for all education users, and Gemini in Classroom, a new suite of no-cost AI tools available for educators.Read More
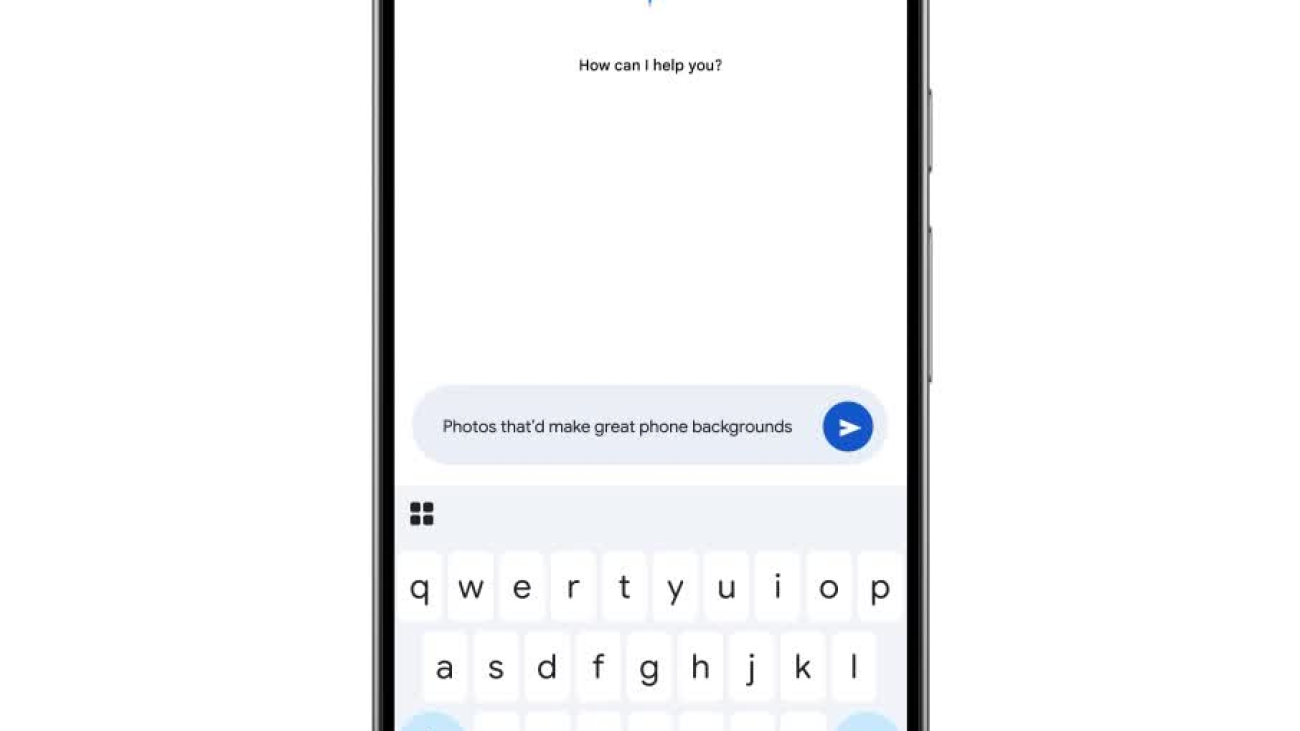
We’re improving Ask Photos and bringing it to more Google Photos users.
 We love seeing how you’re using Ask Photos in early access, like asking “suggest photos that’d make great phone backgrounds” or “what did I eat on my trip to Barcelona?”…Read More
We love seeing how you’re using Ask Photos in early access, like asking “suggest photos that’d make great phone backgrounds” or “what did I eat on my trip to Barcelona?”…Read More
The Google for Startups Gemini kit is here
 Learn more about how startups can use Gemini models and other AI resources from Google.Read More
Learn more about how startups can use Gemini models and other AI resources from Google.Read More
5 tips for getting started with Flow
 Here are five tips for making videos with Flow, Google’s new AI filmmaking tool.Read More
Here are five tips for making videos with Flow, Google’s new AI filmmaking tool.Read More
Gemini CLI: your open-source AI agent
 Free and open source, Gemini CLI brings Gemini directly into developers’ terminals — with unmatched access for individuals.Read More
Free and open source, Gemini CLI brings Gemini directly into developers’ terminals — with unmatched access for individuals.Read More